
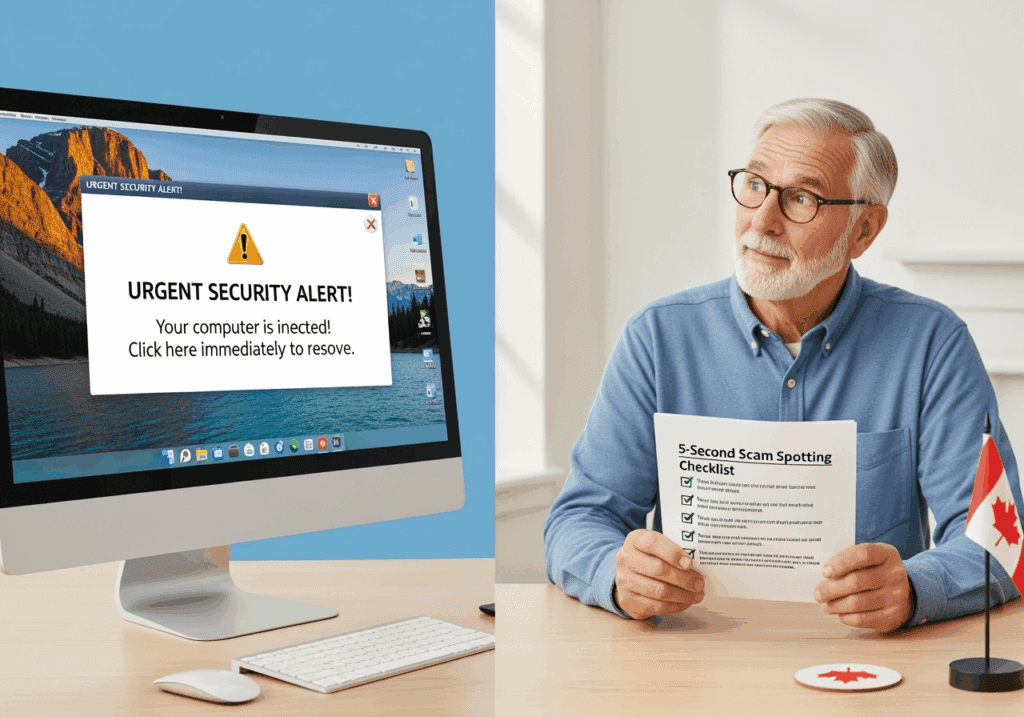
Let me break this down in plain language, so you know exactly what’s happening and what your real options are. [Read more…]
by Tony Whitney

Let me break this down in plain language, so you know exactly what’s happening and what your real options are. [Read more…]
by Tony Whitney
by Tony Whitney
Every business has those IT devices tucked away in storage rooms, old drawers, or even still sitting on your network unnoticed. Forgotten devices may seem harmless, but they can pose significant risks to your business’s security. Let’s take a closer look at why these “forgotten” devices are more of a ticking time bomb than a harmless relic of the past. [Read more…]
by Tony Whitney
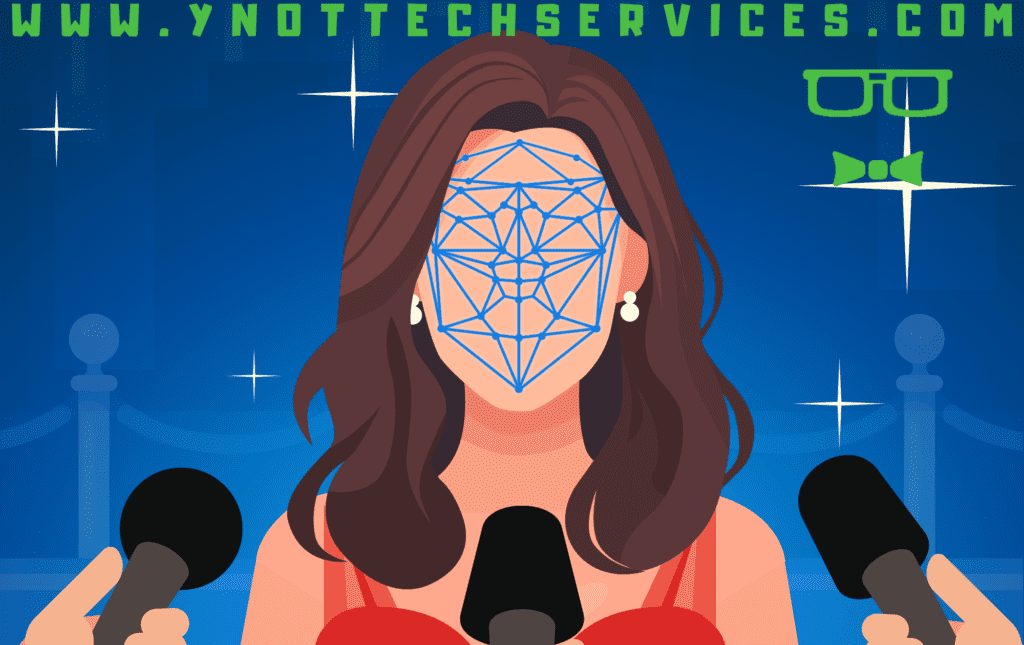 Think That’s a Celebrity Endorsement? It Might Be a Deepfake Scam
Think That’s a Celebrity Endorsement? It Might Be a Deepfake ScamHave you ever seen a video of a celebrity endorsing a new investment or giving away free tickets that seemed too good to be true? You might be witnessing a deepfake AI scam. These scams are becoming more and more convincing, leveraging advanced technology to deceive unsuspecting people.
In this article, we’re going to look at how these scams work, what deepfakes are, and, most importantly, how you can protect yourself. [Read more…]
by Tony Whitney

In today’s digital age, securing your data is more critical than ever. With increasing cyber threats and the potential for data loss, robust encryption tools like BitLocker offer essential protection. BitLocker, a full-disk encryption feature included with Windows, helps safeguard your data by encrypting entire drives. However, to maximize its effectiveness, it’s crucial to understand the importance of backing up your BitLocker recovery code, how to do it, and how to use it when needed.
BitLocker is a powerful encryption feature available in certain editions of Windows. It encrypts the entire drive, making the data unreadable to unauthorized users. BitLocker can be used on internal and external drives, ensuring that your data remains secure even if the device is lost or stolen.
When you enable BitLocker, you are given a recovery code. This code is vital for accessing your data in certain situations, such as:
Without this recovery code, you risk permanent data loss, as there would be no way to decrypt and access the encrypted data.
Backing up your BitLocker recovery code is straightforward. Here’s how you can do it:
If you find yourself locked out of your BitLocker-encrypted drive, you can use the recovery code to regain access. Here’s how:
manage-bde -unlock X: -RecoveryPassword YOUR-RECOVERY-KEY, replacing X: with the drive letter and YOUR-RECOVERY-KEY with the 48-digit recovery code.manage-bde -off X: to decrypt the drive if necessary.BitLocker is a powerful tool for protecting your data, but its effectiveness depends on responsible management of the recovery code. Always back up your BitLocker recovery code and store it in a safe place. Whether you’re an individual at home or an employee in an office, understanding how to handle BitLocker and its recovery process can save you from potential data loss and ensure that your information remains secure.
By following these guidelines, you can take full advantage of BitLocker’s robust security features while maintaining access to your important data when needed. If any of this is confusing to you, don’t worry! We’re here to help:
by Tony Whitney

Have you ever been in the middle of an important phone call or task on your phone when you suddenly see those dreaded words, “SOS only” or “No Signal”?
Most of the time, it’s simply due to poor signal strength in your area or a temporary glitch with your carrier’s network. But what if losing your phone connection wasn’t so innocent?
What if an unknown hacker actively removes you from your mobile number to take it over for their own malicious purposes? This is the frightening reality of a cybercrime called “SIM swapping,” and it’s a growing threat that has affected many unwitting victims. [Read more…]
by Tony Whitney
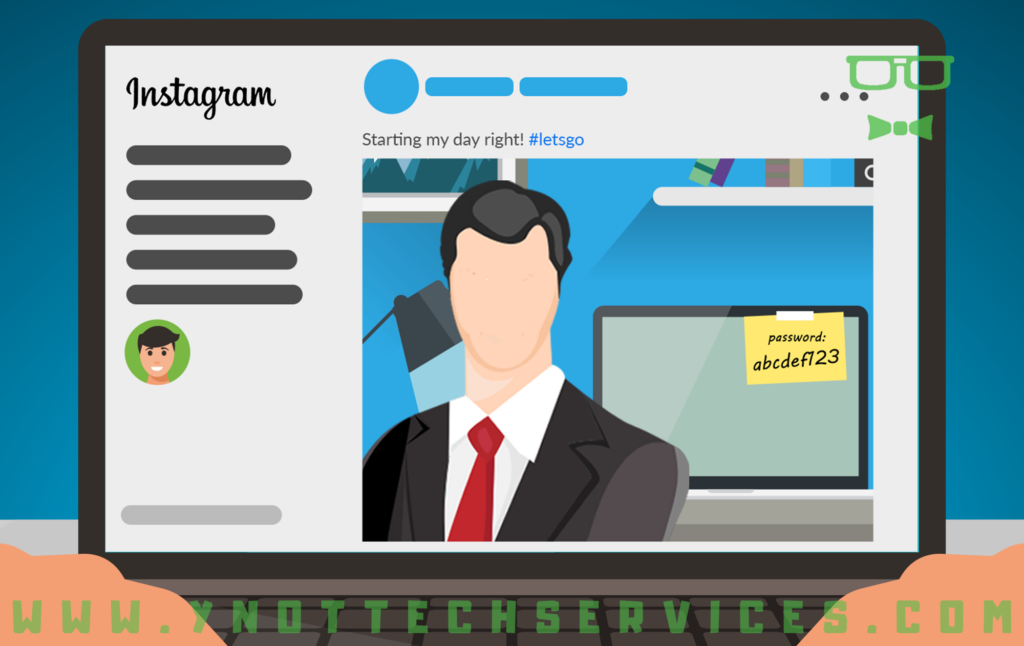 Casual Social Media Posts and Hidden Dangers
Casual Social Media Posts and Hidden DangersSocial media is a powerful marketing tool for small businesses, allowing you to share updates and engage with customers easily. However, what you share on platforms such as Facebook and Instagram could put your company at risk of a cyberattack. [Read more…]
by Tony Whitney
 6 Fresh Ways to Mark National Computer Security Day
6 Fresh Ways to Mark National Computer Security DayNot worrying about bad actors infiltrating business technology would be a cause to celebrate, but that’s not a reality. So, instead, National Computer Security Day reminds us to promote computer security.
As technology advances, securing electronic devices and online systems grows more complicated. We now have October as Cybersecurity Awareness Month to encourage education and motivation. Also, since 1988, November 30 has been devoted to keeping online data safe and secure. [Read more…]
by Tony Whitney
The advent of modern data has offered many advantages, yet all that data also presents a formidable challenge: data sprawl. When you lose control of your data, you risk compromising productivity, security, and compliance. This article shares strategies to help you address the thorny issue of data sprawl.
You’re probably dealing with data sprawl if any of the following sound familiar:
These examples capture what it’s like to try and work amidst data sprawl. These issues drain productivity and waste resources. Data sprawl can also leave you open to cybersecurity vulnerabilities and compliance concerns. After all, you can’t back up or recover data you don’t know exists in the first place.
Regain visibility to control support, streamline processes, enhance security, and improve efficiency. The following strategies can help.
Start tackling your data sprawl situation by mapping out your existing data landscape. Thoroughly assess your data sources, storage locations, and data repositories. Once you have an idea of where your data is:
Employees now work on-site, at home, and in other remote locations, or perhaps all three, which often causes data sprawl. A staffer might use their desktop computer in your office but their personal laptop at home. Even if everyone works in the same place, they might use desktops, laptops, tablets, and smartphones.
Migrating to the cloud provides access to centralized storage. Avoid version-control concerns with everyone accessing the same data, no matter where they are. You can also ensure data is securely backed up, no matter the user’s device.
Another way to keep employees on the same page is to give everyone access to the same business tools. For instance, Microsoft Office or Google Workspace can simplify communication and collaboration, especially in a bring-your-own-device (BYOD) workplace. Cloud-based tools can create cohesion, as everyone logs into the same software to get their jobs done.
In a data sprawl situation, it’s easy to lose track of where data lives and who has access to it. Then, when you move on to that next project, you might leave that old data unattended. If it’s breached, you might not even know.
Instead, track and log data to understand what’s where and who can get at it. When a project is over, have a policy in place for properly archiving or deleting data that is no longer needed.
Is data overwhelming your business? Our IT experts can help. Contact us to support your data management strategies. We’ll get to know your systems and provide strategies to effectively combat data sprawl. Book an appointment today:
by Tony Whitney
 Finding Business Balance on the Sliding Scale of Security
Finding Business Balance on the Sliding Scale of SecurityEvery day there’s some new malware or data leak or hacker exploit revelation. Your business is vigilant, but it feels like you always have to be doing more about cybersecurity to remain protected. Meanwhile, you want to balance security measures with usability, convenience, and cost. That balancing act puts you somewhere on the sliding scale of security. [Read more…]

